Some small and medium-sized businesses underestimate security because they believe they are not an interesting target for cyber attacks and that business security goes beyond their budget. Unfortunately, this approach is why small businesses are often victims of attacks. Mastering at least basic security is not a superhuman task.

The topic of one of the latest eWay-Blog articles was data protection and current security trends. The article contained some tips for data protecting each for individuals. From a company perspective, computer literacy and security of every employee are very important. However, alongside user-level security, every company should also, or above all, have enterprise-level security.
Most frequent threats
Before a company begins to address how to protect themselves, it should know what potential threats exist so that it can then address protection from all kinds of attacks. There are many kinds of cyber attacks. The most common are:
- Malware
Malware, and other types of malicious software, such as spyware, ransomware, or viruses, are typically installed on a PC without the user's knowledge by clicking on an untrusted link or email attachment. The infected device can be used for spamming, the data can be damaged or erased or the data (including passwords) could even be sent without the user's knowledge. Or the device can be encrypted to require a ransom as a condition for restoring the access.
- Phishing
Phishing is a fraudulent technique used in online communication to obtain sensitive information, such as passwords and credit card numbers, or to install malware. For example, fraudsters use phishing sites that look like banking login pages, or email communication asking for password changes that appear to have been sent by an IT administrator. To avoid such situations, make sure that you use DMARC setup to protect your email security from phishing.
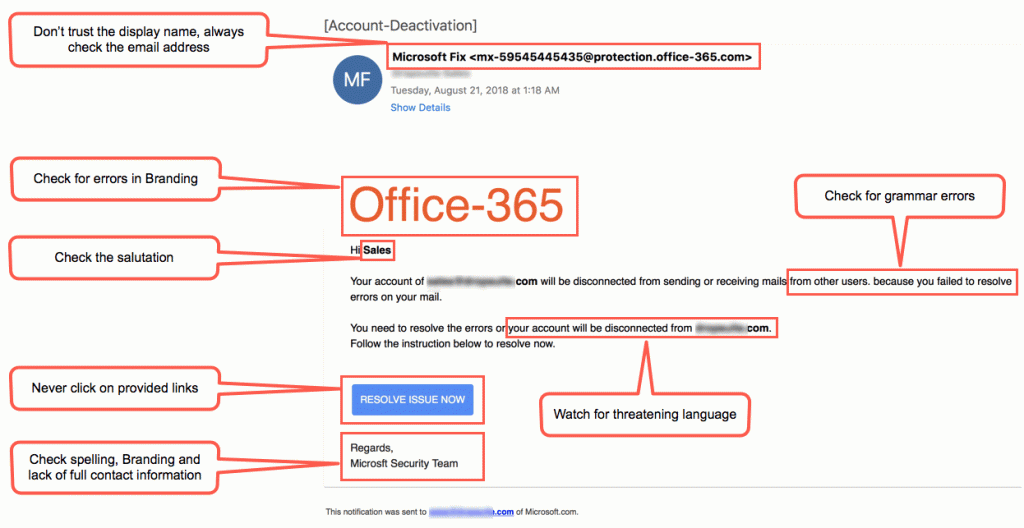 Example of fraudulent phishing e-mail impersonating MS Office e-mail.
Example of fraudulent phishing e-mail impersonating MS Office e-mail.
- Man in the middle
In the so-called MitM attacks, the fraudster eavesdrops on the communication between two systems. This usually happens on public Wi-Fi networks or websites with a fraudulent certificate (which should always be "https").
- DDoS
Under the name ‘Distributed denial of service’, there are various types of attacks that overwhelm the server so much that it interrupts its operation. For example, for e-shops, a server blackout can mean a significant loss of revenues.
- SQL injection
It is an attack on web SQL databases. In this case, the fraudster uses errors in the site code and puts malicious code on the server. This is a common problem for websites and e-shops that use CMS systems (such as WordPress, Joomla and others).
- Zero day attack
This term does not mean a specific technique, but the time it takes to exploit a certain vulnerability of the software before the release of a fix that corrects the vulnerability. This phenomenon cannot be 100% avoided, as Roman Štefko, CTO of eWay System says: “Hackers are always one step ahead. You can meet all conceivable security standards, but if there is a security hole in your system and the attackers find it, basically the attack cannot be avoided.“ Roman Štefko also suggests some principles about how to make some mistakes in the system unusable in real life.
Security measures for businesses
Now you know the real threats to your business. That means that it is time to go through at least the basic measures. If you don't use any of them in your business, you might want to consider changing it.
- Firewall
A firewall is a software or device that controls and possibly blocks data traffic between the work network and the Internet. It is the cornerstone of a company's security that, when properly set up, prevents the spread of viruses, malware, and other threats.
- Security software
In addition to the firewall, it is important to use other tools such as antivirus, anti-malware and cryptographic software, password management applications, and other security software as needed. Against the mentioned SQL injection and other attacks, it is appropriate to secure WordPress and other web applications by so-called security plugins.
- Staff training
In most companies, people are the weakest point as far as security is concerned. It's logical. Not every position requires advanced IT knowledge. For example, many employees often do not realize that they should not use USB flash drives of unknown origin in the work network, for example, as they may contain malicious software. They do not recognize fraudulent sites or emails and become the victims of phishing. Or they do not set up strong passwords and use an insecure communication tool to send credentials to their colleagues.
- Company policy and documentation
Training employees in data security is one of the key measures. However, passing on information alone is not enough. Especially SMEs often leave the subsequent application of security measures to the employees themselves. Unfortunately, the intuitive approach does not pay off. It is necessary to introduce specific procedures, policies, and documentation in the company so that security measures are adhered to without exception.
One of the important principles that every business should adopt is to regularly update all applications. As mentioned for zero day attacks, there is no absolute protection, but this habit will help you avoid a lot of application security vulnerabilities.
Another important element is the previously mentioned password management applications. Most users use the same password for multiple systems, and if an attacker succeeds in obtaining the password, it is easy to try whenever they claim to be someone else. Password management applications register access to individual programs and with a few mouse clicks they can pre-fill the right password, which can then be any set of all kinds of characters.
- Backup
As in life, it is sometimes good in business to be prepared for the worst. That's why it's very important to back up your business data on a regular basis, whether on your own server or on the cloud. For example, for e-shops, regular backups are an absolute necessity in the case of these DDoS attacks.
Security certificates
Cyber attacks are increasingly common and pose a risk of huge damage to many companies or institutions. And as Bureau Veritas, a security certification company, points out, the damage must not always be counted in cash: “Hospitals that until recently have not been covered by the Cyber Security Act and their systems are vulnerable are very vulnerable to attacks. This can be shown by a recent case in one hospital, where a blackmail cryptovirus attacked a computer system of a medical facility and prevented, for example, from carrying out planned operations. Companies and institutions that are certified according to ISO 27001 have a significant lead in meeting the requirements of the Cyber Act. ”
Certification for the security of information and personal and company data is not required by law for most companies. However, completing a security audit can motivate a company to improve its own security measures. Not only does it win the trust of potential and existing clients, some multinationals or state-owned enterprises even require security certificates to win the contract.











