How to Become Compliant With the Data Privacy Laws And Get Ahead of Any Risk

Keeping client information private requires more than simply following the law in the legal profession. Data security breaches may devastate a company's reputation and ability to retain customers and workers and manage consent to share their information. It is also helpful in avoiding possible legal action and regulatory investigations, including data security, if a company has comprehensive data privacy policies and procedures. If a firm can keep data security events at a minimum, it will get significant reputational advantages.
The Importance of Maintaining Data Security
In today's information-based economy, data is a precious commodity, and its collection and exchange may be lucrative commercial endeavors in their own right. To safely and productively use the data it gathers, a company must have measures to ensure the data is maintained securely and users are not subjected to unsolicited monitoring.
Customers have become more aware of the possible drawbacks of collecting ever-increasing volumes of data about themselves, which corporations are doing. Protecting private information is now more vital than ever, and companies should give considerable attention to the data privacy processes and policies they have in place for various reasons.
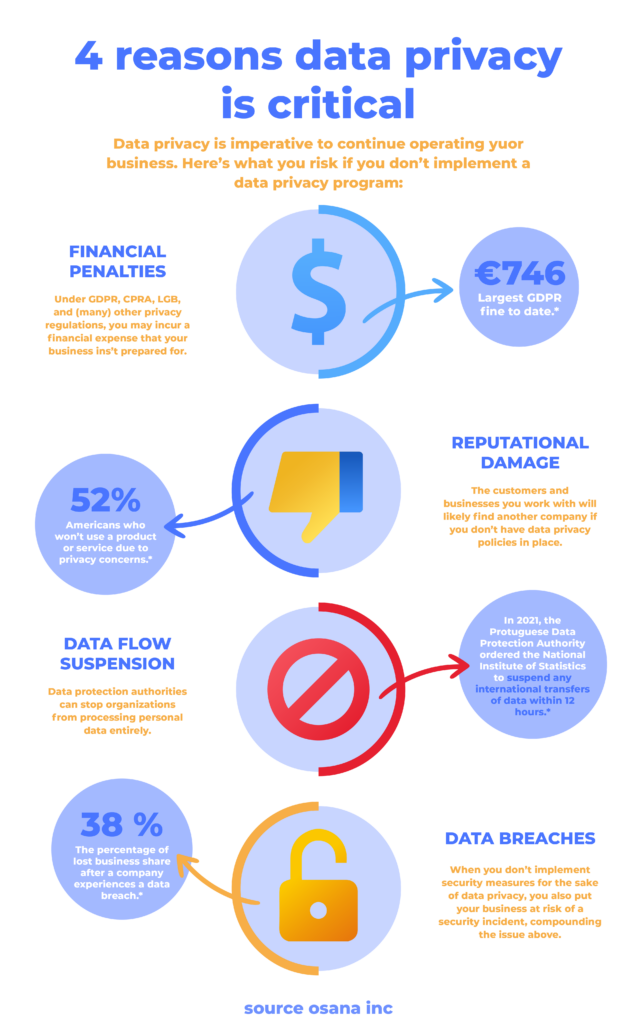
The regulatory environment has resulted in new challenges for enterprises. Data privacy rules like California's CCPA and the EU's GDPR. It has had a profound impact on how companies may gather, keep, and manage personal information about customers. These laws cover everything and give the people they protect a level of legal protection they didn't have before.
In addition, concerns about the privacy of users' data have been raised due to the COVID-19 incident. Information on the workers' health and travel plans, including personal details, is collected by businesses. To prevent the virus's spread. These firms must comply with the GDPR (GDPR). Other vital agencies include the ADA, CCPA, and HIPAA.
Companies frequently violate data privacy regulations because their security processes can't keep up with cyber threats. A growing number of cyber thieves, hackers, and government cyber terrorists are developing more sophisticated methods to launch attacks on organizations using the internet. As a firm, you must protect client data. You must legally gather, store, handle, and get rid of junk data. You must also have comprehensive data protection policies and processes to safeguard your customers' data from harmful or unauthorized usage.
In this primer, we'll cover the importance of protecting sensitive company information, the laws that apply to organizations in the United States, and the measures that comply with those laws while safeguarding vital company assets and good name.
Because of the increasingly dangerous environment, your legal team must be aware of your duties to secure the personal data of your customers and your employees. You must understand the consequences of breaking such responsibilities and the necessary preventative and corrective safety actions.
The difficulties involved in maintaining privacy in the modern legal system
In 2017, 1139 data breaches exposed 174,402,528 records in the U.S. When regulatory penalties are coupled with the cash losses resulting from a violation, the overall expenses that a firm may incur due to the breach are startling.

Companies that operate outside of the United States and handle customer data are required to take additional precautions against data breaches on a global scale. Research by the Ponemon Institute found that 42 percent of firms in the United States had not taken any measures to prepare them for a worldwide data breach.
Understanding the full scope of the US and foreign privacy regulations may be challenging, particularly given that different privacy rules often cover various data sets. In the US, HIPAA safeguards patient health information. In the United States, many companies' compliance and legal divisions aren't up to speed on the nuances of data privacy regulations and don't know how to deal with them. In addition, the danger of incurring fines for non-compliance rises as a direct result of a growth in the number and scope of the legislation.
A collaborative effort on a global scale
Regarding protecting personal information and privacy, Europe is now at the vanguard. Companies that violate the General Data Protection Regulation (GDPR) in any way, such as by improperly processing personal data or disclosing it to other parties, are subject to harsh financial penalties. Another global data protection regulation is Canada's PIPEDA. The US has state and federal privacy laws, and sector- and data-specific restrictions differ.
The departments of legal affairs and compliance are responsible for determining whether laws and regulations are applicable on the international, national, and state levels. Where exactly do you start?
Your organization or group needs a complete compliance program.
These components will be necessary for a solid framework that protects the privacy of your customers' and workers' data and consists of:
Having a Comprehensive Strategy for Compliance Overall
Many businesses do not possess a complete, integrated, quantifiable, and centralized plan to achieve compliance with data privacy regulations. It is accomplished by establishing an elevated set of principles and paperwork specifying the actions the organization will take about individuals' private information (as defined by applicable laws). All of the organization's most important stakeholders and departments must be represented.
Having Subject Matter Experts for Compliance on Hand (SMEs)
No one can't be an expert on the many rules that must be complied with. Designating SMEs to take on the role of experts for HIPAA or GDPR. This plan assures that a singular source of knowledge designs policies and procedures that are legally compliant. Dedicated small and medium-sized enterprises (SMEs) have the potential to act as the providers of compliance documents in your region.
Taking an Inventory of, and Conducting an Assessment on, Personally Identifiable Information (PII) and Other Forms of Sensitive Personal Information (SPI)
When gathered, personal information has to be labeled and identifiable in some way, and businesses are obligated to give the means to keep track of it. It will assist you in locating personal data and protecting it acceptably in compliance with legal requirements and suggested standards.
Putting in Place Procedures and Policies for the Protection of Data
A company that complies with privacy regulations has solid, technological, and physical security precautions to protect privacy, security, and data availability. Information security must be continuously evaluated, monitored, and updated. Data exchange is governed by a stringent set of regulations and procedures.
Creating a Strategy and Plan of Action in Response
Even if all compliance regulations are followed, no system will ever be flawless. Unfortunately, even the most advanced defenses can't stop persistent cybercrime and data breaches. An efficient data breach response strategy and escalation procedure may lessen the damage done by an intrusion by providing a means of mitigating its effects. Training on these strategies and the proper use of escalating channels are available for employees responsible for responding to security breaches. As proactive preventative steps against a recurrence of the incident, the remedial actions outlined in the action plan need to be implemented and recorded.
Maintaining Appropriate Documentation for Compliance
The documentation of compliance strategies and procedures is correct. Documents, reports, and data may be stored in and managed using several different content management systems, such as Microsoft SharePoint, OneDrive for Business, or one of the many others available. It would be fantastic if there were a worker whose only responsibility was to manage document compliance and security.

Providing Evidence That We Are In Compliance
You need to exhibit your conformity to any inquiries, whether from outside or inside. Compliance must be easily verifiable and readily available via reports and documentation. A procedure for reporting non-compliance and a method for escalation should be in place. Confidentiality rules are screened through adequate monitoring, auditing, and user controls.
Move quickly to address questions about compliance with data privacy regulations.
Emerging trends in the corporate and technological landscapes will bring about significant changes that will make it more challenging to safeguard individuals' personal information. Controls and management will have difficulty keeping up with big data and its enormous datasets. Because of the exponential growth in the volume of international data transfers, additional security precautions will need to be included in the network and Internet infrastructure. The emergence of stricter consent requirements is on the horizon of the regulatory and legal landscape. The control individuals have over their data usage and how it is used will expand. Many U.S. firms are still figuring out how the GDPR impacts them and what new technologies they need to comply with.
Your legal team will have the peace of mind to know that it completely satisfies its data privacy duties if it takes the time to fully grasp the legal environment that affects personal data and implement a comprehensive compliance strategy to adhere to it.
Utilize the resources provided by Practical Law to gain a comprehensive understanding of the legal environment affecting private information. Implement a complete compliance system to ensure that you fully comply with it. It will let your legal team know it meets all its data privacy commitments.
About the Author:
Darakhshan Roohi is a Pakistan-based content specialist focused on cryptocurrency, Fintech, and ERP-based business solutions. She is a freelance writer and part of groundbreaking cryptocurrency content presently under work!










